The trend of the last few years suggests that many services are moving from traditional desktop installations to the clouds. was no exception and electronic signature. However, the migration of ES to the clouds is perceived by the community of users and experts is still very ambiguous. Among the undoubted advantages of new cloud solutions, the issues of providing information security. However, neither technology nor legislation stands still, and soon we can expect a new round of development of electronic signature with the participation of cloud computing.
Electronic signature as the basis of legally significant electronic document management
An electronic signature (hereinafter referred to as an ES) in accordance with Federal Law No. 63-FZ of 04/06/2011 is a mandatory legally significant requisite of an electronic document. In addition to this, the law also says that the ES is an absolute analogue of the actual manual signature put on paper document. In view of this, it is logical and quite reasonable to assume that electronic document turnover is a real alternative to traditional office work in general and in particular to individual processes of concluding and confirming various transactions, agreements, agreements, contracts, etc.
According to the above federal law, ES, as a mandatory element of EDI, is designed to provide three key tasks:
1. Provide unique identification of the signatory
document;
2. Provide protection against unauthorized changes to the document;
3. Ensure the legal force of the electronic document.
The legal significance of the use of electronic signatures is enshrined in a number of domestic normative documents. Here are a few key links:
- Art. 160, 434, 847 of the Civil Code of the Russian Federation, which regulate practical use electronic signatures in document circulation.
- · Federal Law No. 63-FZ "On Electronic Signature" of 04/06/2011. The main and framework law describing the general meaning of the use of electronic signatures in transactions different nature and provision of services.
- · Federal Law No. 149-FZ “On Information, Information Technologies and Information Protection dated July 27, 2006. This document specifies the concept of an electronic document and all related segments.
- · Federal Law 402-FZ "On Accounting" dated 06.12.2011. The legislative act provides for the systematization of requirements for accounting and accounting documents in in electronic format.
- · According to paragraph 3 of Article 75 of the Arbitration Procedure Code of the Russian Federation, documents obtained using the Internet information and telecommunication network and signed with an electronic signature are allowed as written evidence in arbitration disputes.
All of the above facts and arguments mean that, using the ES, we can always clearly know by whom and when the document was signed, be sure that no changes were made to the document after signing, and in case of disagreement between the parties and subsequent litigation proceedings to ensure the non-repudiation of the fact of the transaction (conclusion of a contract, etc.).
Currently, the legislation establishes three options for the use of ES in the territory Russian Federation, This:
- · Simple EP;
- · Reinforced unqualified ES;
- · Reinforced qualified ES.
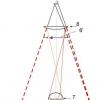
How do they differ and what kind of electronic signature can and should be used to make financial transactions? Below we will analyze them. And so, let's start (see Figure 1)
1. Simple electronic signature
A simple signature, or as it is often called a “login-password” link, is an electronic signature that, through the use of codes, passwords or other means, confirms the fact that an electronic signature has been formed by a certain person.
A classic example is when you enter your credit card pin, say the passphrase (voice tag) in telephone conversation with the bank's call center and the like - all this will be yours Simple Electronic Signature. In other words, the only function of such a signature is confirmation of authorship , personal identification. Simple EP provides a basic level of protection and authentication. Eg. She signature is used to gain access to features Single portal of public services. A simple electronic signature cannot be used categorically when signing electronic documents or in the state information system (GIS) that contain state secrets.
2. EP is reinforced UNQUALIFIED if the following conditions are met:
- obtained as a result of cryptographic transformation of information using an electronic signature key;
- allows you to identify the person who signed the electronic document;
- allows you to detect the fact of making changes to an electronic document after the moment of its signing;
- · is created using electronic signature means.
Reinforced UNQUALIFIED ES allows you to determine the author of the signed document and prove the immutability of the information contained in it. IN unqualified electronic signature cryptographic algorithms are laid down, which provide reliable protection of documents in accordance with Russian GOST for encryption. Such a signature is quite suitable for internal document management in a company, as well as for sending electronic documents from one company to another. Unqualified electronic signature also suitable for participation in electronic trading.
3. And, finally, the third option, when EP is enhanced qualified, if it meets all of the above features of an unqualified ES and the following two additional features:
- The electronic signature verification key is specified in qualified certificate;
- To create and verify an electronic signature, electronic signature tools are used that have received confirmation of compliance with the requirements established in accordance with this Federal Law
It is worth noting. What software required to work with CEP must be certified by the Federal Security Service. Therefore, a qualified electronic signature gives documents full legal force and complies with all requirements for the protection of confidential information. Regulatory authorities, such as the Federal Tax Service, the Pension Fund of the Russian Federation, the FSS, recognize the legal force of only those documents that are signed by a qualified electronic signature
Figure 1. Types of electronic signatures

Over the past few years, the trends in the transition from operating your own IT infrastructure to using cloud computing have become firmly entrenched in the IT industry. This is, first of all, the replacement of traditional IT systems initially deployed on the material and technical base of each hotel company taken with on-demand services, tk. SaaS, PaaS and IaaS. According to a recent study "Cloud services in the corporate sector, Russia 2017". from SAP and Forrester companies, cloud technologies in Russia will grow faster than the entire IT market taken as a whole: thus, at an average annual rate of 21%, the cloud market will grow 3 times compared to 2015. The report states that large businesses are currently as ready to use cloud services as possible: in this segment, over 90% of respondents know about cloud services, in small businesses - over 70%. In large businesses, 54.5% of respondents use simultaneously cloud services from two or more categories, in medium businesses - 50%, in small businesses - 43%.
The current situation with the use of cloud ES in RussiaMost recently, in June 2017, it became known that the FSB, together with Rostelecom, was creating an electronic signature that would “blow up and turn the market upside down”. The idea is the same, to create an electronic signature that does not require the use of a token (carrier on a flash drive). Mikhail Bondarenko, director for e-government at Rostelecom, spoke about this. “I have information from colleagues from Lubyanka that a solution should be released by the end of the year that will allow making trusted digital signatures cloud-based,” he said, without giving any details, but contrasting this solution with electronic signatures on tokens that are common today. “In our opinion, this will blow up and turn the market for trusted authorization and identification,” he added. But there is a nuance, in addition to the use of "clouds", it is also planned to use biometrics, i.e. individual biometric characteristics of each person as parameters for his unique authentication.
According to the same source according to Bondarenko - “ It is assumed that Rostelecom will become the operator of this platform and will conduct a pilot experiment with banks for two years, during which time biometric identification services will be provided to them free of charge., noting that about ten banks, including Sberbank, VTB and Gazprombank, are participating in the pilot that has already started.
At the same time, the operator intends to complete the creation of the platform by the end of 2017. In addition, only from January 1, 2018, amendments to 115 the federal law allowing the use of biometric identification in financial sector- for opening and closing accounts, placing and withdrawing deposits, transfers, etc. Thus, according to the top manager, the idea of creating a “national bank for identification and authorization” of Russian residents on the basis of the national biometric platform is already being considered.
Expert comments:
“According to our estimates, the total number of electronic signature users in Russia exceeds two million. The technology of "cloud" electronic signature, which appeared several years ago, makes this tool more accessible for business. This is confirmed by several tens of thousands of SKB Kontur customers who have made a choice in her favor,- says the expert Kazakov.
A "cloud" electronic signature has all the properties of a regular one, only it is stored not on a flash drive or computer, but on the Internet - on a special secure server, "in the cloud",- says Igor Chepkasov, founder and president of the National Cryptocurrency Development Fund. - The signing and encryption of the document also takes place there, therefore such an electronic signature does not require the installation of special software on the computer. Chepkasov notes that one of the key advantages of the "cloud" signature is the ability to sign documents and send them from anywhere in the world and from any device.
Anton Elikov (Merkat project) notes that an electronic signature “in the cloud” is something that many of us use every day without even noticing. “The most striking example is the authorization mechanism in mobile and Internet banks, when, after entering a password, you are sent a one-time PIN code via SMS. Such a two-level authorization, in essence, can already be an electronic signature, ”- says the expert.
Igor Chepkasov talks about the possibilities of using ES in new services, for example, built on the technology blockchain namely, smart contracts. “Decentralization, the fundamental principle of the technology, provides absolute protection against compromise and unauthorized access to any document and the signature itself, since each such block element (signature, document, archive, etc.) is located in a strong chain of numbered blocks protected by the most complex cryptographic code", he says. So, according to the expert, it is impossible to make changes to the block already put into circulation; a smart contract is an electronic algorithm that describes a set of conditions, the fulfillment of which entails certain events. “His work is based on the creation and application of so-called low-trust protocols, where the protocol algorithm uses only software, and the human factor is excluded from the chain of decision-making as much as possible - the person here acts exclusively as one of the parties involved in the implementation of the contract. For example, when sending payments, the execution of the contract is impossible without receiving the number of electronic signatures specified in the contract., he notes.
Currently, certificates of electronic signature verification keys (SKP) are issued on special media, said Mikhail Evraev, Deputy Head of the Ministry of Telecom and Mass Communications. At the same time, the average cost of such an SPC is about 5 thousand rubles. "The cloud electronic signature system will allow you to create a signature without a material carrier, which will significantly reduce the cost of its use and increase the security of use,"- explained the Deputy Minister.
The situation was also commented on by the Internet Ombudsman Dmitry Marinichev, who is sure that a real revolution will take place in digital signature technologies, as happened several years ago with information storage devices. For example, back in the 90s, films were sold on VHS tapes, in the 2000s they appeared on CD, then on DVD, and ten years later they are finally distributed on flash drives and on the Internet.
Prospects for the use of cloud ES for the banking industryAn electronic signature was conceived as a universal means of confirming the legal validity of transactions, and in view of this, it has a wide range of applications, from using the public services portal to providing electronic document management between organizations and state regulatory authorities. For the banking industry, ES by individuals and legal entities most often used to make financial transactions through RBS services. This includes online access to Personal Area through web technologies and mobile banking, i.e. account management through a socialized application from smartphones and tablets.
For example, EP for individuals in the largest federal bank - Sberbank makes it possible for a banking organization to reduce paper turnover and increase the speed of customer service. That is, during the opening of a deposit, instead of setting a signature on 4 different documents, the visitor will need to dial his PIN (password to the ES) 1 time. This type technology will be able to provide dual client identification using a passport and using a card with a PIN code that only the owner can know. This will also prevent potential fraud. So, according to internal data of Sberbank relevant for 2014, within twelve months after the launch of such a service, more than three million operations were performed by residents of Moscow using an electronic signature.
The procedure for obtaining the corresponding key of the electronic signature of the Bank of Russia is quite simple, you need to go through online registration on the specialized website "Sber Key". So the bank gives the right to an electronic signature to any of its owners to take part in the auction and place it on the necessary electronic resources personal statements.
Another illustrative option for the mass use of cloud ES can be available in the Sberbank Business Online Internet bank, which has become Sberbank's official tool for electronic signature multilateral and bilateral agreements between any legal entities and individual entrepreneurs (IP) - the so-called inter-corporate EDI. As he explained, thanks to this system, the labor costs for processing one document are reduced from 2-3 minutes to 10-15 seconds. In addition, by eliminating paperwork, the company can significantly reduce the cost of stationery, rental of warehouse space, replacement Supplies for office equipment, etc.
Cloud ES security issuesDespite all the tangible advantages of using ES in the clouds, this concept has not found wide support among information security experts. Thus, according to some experts, the use of ES tools in a mobile phone poses a significant security threat. You don't need to be an expert to see the depressing statistics of the growth in the number of mobile malware intercepting user SMS messages, disguising itself as official mobile banking applications and performing other unauthorized actions without the user's knowledge.
In view of this, only a trusted (isolated) environment in which the user and technical means at the time of interaction are protected from outside interference. It is difficult to call a mobile phone such a trusted environment - the user can install any application at his discretion. The situation is worse, if only if the operating system of the device is rooted. However, there is a way out - as already described earlier, this is the use of a special SIM card integrated with the EP.
When using remote banking services, attackers often carry out a “man in the browser” type attack, which is a private implementation of a “man-in-the-middle” attack, when, by replacing the details of a legal payment, showing the user the correct data, and sending their own, spoofed, to the bank. With the new security feature, such an attacker's trick will no longer work - having received the details, a special applet on the SIM card will display them on the phone screen and request a PIN code. Having visually checked the correctness of the details, the user enters the PIN code of his electronic signature for confirmation, signs them and then sends them back to the gateway, which transmits the information to the bank.
Sergey Gruzdev, CEO Aladdin R.D., a developer of domestic cryptographic protection systems, highlights another way to use this technology - “In addition to authentication and signing documents, the developed system can be used to notify a bank client about transactions with his account, which has become especially relevant in the light of the entry into force of the ninth article 163-FZ "On the national payment system" . Unlike the most popular this moment method - SMS informing, in this case banking secrecy is guaranteed (no one can read the notifications, neither by infecting the smartphone with a virus, nor even by replacing the base station), and the substitution of messages by intruders is excluded.
Another problem remains, when, for example, in case of loss and deliberate theft of the phone and the PIN code saved in the notes or other internal memory of the phone. In this case, the attacker will be able to spend all the money from at least the owner's mobile account, and, for example, sign documents binding the subscriber, for example, pay for purchases on credit at one of the popular online stores. However, these risks are quite confidently prevented in much the same way as with payment and credit cards. The owner of the account (card) can limit the daily volume and content of transactions allowed from this SIM card, as well as use the option to disable his ES for a temporary period while he does not use it.
This article is a continuation of the article and covers cryptographic solutions:
- cloud signature
- separate browsers with Russian cryptography
- separate mail clients with Russian cryptography
- Russian cryptography in frameworks, platforms, interpreters
- desktop cryptographic applications
- means of forming a trusted environment
cloud signature
The cloud signature concept involves storing the private key and performing the data signing/encryption procedure directly on the server.For safe use cloud signature it is required to solve the problem of strong client authentication when accessing its private key and the problem of secure storage of the private key on the server. An example of such a solution is CryptoPro DSS, which supports Rutoken WEB (strong two-factor authentication) as one of the authentication options, and uses HSM to store the private key.
| Platforms | Any with a browser and Internet access. Authentication method can impose restrictions |
| EDS, encryption, hash function, imitation protection, HMAC, VKO | |
| Integration with PKI | |
| EDS mechanisms | Sending the document to the server, signing the document on the server, returning the signature WEB API for integration into third-party services SOAP interface for integration into third-party services |
| Authentication mechanisms | according to the Rutoken WEB authentication protocol by SMS Login: Password |
| Secure Message Formats | PKCS#7, CMS, XMLSec, CADES |
| Browser Integration | 100% |
| Mobile platforms | iOS, Android |
| Command line utility | Eat |
| Key vaults | HSM, secure database |
| It is possible to authenticate in the cloud signature service by tokens (CryptoPRO DSS and Rutoken WEB) | |
| Examples (GOST) | CryptoPro DSS "Cloud" signature SKB Kontur sign.me service |
Problems:
- strong authentication in the service
- private key protection guarantees against unauthorized access
- system security reduction -> application limitation
- cross-platform, cross-browser
- convenience for the end user - nothing needs to be installed and configured at all
- easy integration into Information Systems(WEB API)
Separate browsers with Russian cryptography
Browsers based on open source Mozilla FireFox and Chromium projects use NSS or OpenSSL as a cryptokernel. OpenSSL supports Russian crypto algorithms. For NSS, there are also developments that provide support for Russian crypto algorithms. Some time ago, full-featured browsers with support for Russian cryptography appeared on the market.Such a solution has a great, currently unclaimed, potential, as it allows you to create secure standard WEB clients for systems with high security requirements. Another advantage of this browser is its "portability". Given the existence of secure USB tokens with FLASH memory, secure solutions have been created in which the most critical operations with the private key are carried out on the “board” of the USB token, and the browser itself is stored in its FLASH memory protected from modification. Such a solution other than high level security is very convenient to use.
Based on NSS
The picture shows the solution architecture implemented in the NSS aToken extension project.| Specification | NSS using PKCS#11 tokens, software and hardware |
| Platforms | |
| Algorithms and cryptographic protocols | |
| Integration with PKI | X.509, PKCS#10, CMS, CRL |
| EDS mechanisms | |
| TLS-GOST | |
| Secure Message Formats | PKCS#7, CMS |
| Browser Integration | 100% |
| Mobile platforms | iOS, Android |
| Key vaults | |
| Interaction with USB tokens | |
| installation | |
| Examples (GOST) | Mozilla FireFox, Chromium by Lissy atoken project by R-Alpha (Mozilla FireFox) CryptoFox (PKCS11 token based on CryptoPro CSP) |
Problems:
- only one application with Russian cryptography - the browser itself
- browser update
- retrain the user to use a custom browser
- certification (no precedent)
- cross-platform
- transparency of use for the user
- no limits for back end developers
- no installation required, run from FLASH-memory USB-token
Separate email clients with Russian cryptography
Individual mail clients with Russian cryptography allow you to implement the protection of correspondence using an electronic signature and message encryption for a subscriber / group of subscribers (S / MIME). This solution is convenient to use in systems built according to the "point-to-point" principle, in which information is exchanged directly between subscribers, and the server is used only for message routing.| Platforms | Windows family, GNU\Linux, OS X, iOS, Android |
| Algorithms and cryptographic protocols | EDS, encryption, hash function, imitation protection, HMAC, VKO, TLS |
| Integration with PKI | X.509, PKCS#10, CMS, CRL |
| EDS mechanisms | Calling browser built-in functions from JavaScript |
| TLS-GOST | Built into the library and supported by the browser |
| Secure Message Formats | PKCS#7, CMS |
| Browser Integration | 100% |
| Mobile platforms | iOS, Android |
| Key vaults | Browser storage, USB tokens |
| Interaction with USB tokens | Key and certificate storage Using hardware implementation of algorithms |
| installation | The installer generally does not require system administrator rights portable. For example, launching a browser from the FLASH memory of a USB token |
| Examples (GOST) | Mozilla ThunderBird by Lissy DiPost from Factor TS |
Russian cryptography in frameworks, platforms, interpreters
Microsoft.NET
Class extensions
The platform has a set of cryptographic classes that provide mechanisms for extension by third-party algorithms. The most well-known solution on the market for extending the Microsoft.NET platform with Russian cryptoalgorithms is the CryptoPro product. NET, which is an add-on for CryptoPro CSP.Installing CryptoPro.NET allows you to use Russian crypto algorithms, for example,
in WEB services based on ASP.NET, SOAP services, in MS.Silverlight client browser applications.
| Platforms | Microsoft.NET 2.0 and later |
| Algorithms and cryptographic protocols | EDS, encryption, hash function, imitation protection, HMAC, VKO, TLS, SOAP |
| Integration with PKI | X.509, PKCS#10, CMS, CRL |
| EDS mechanisms | A set of classes. There are fully "managed" implementations. There are implementations based on Crypto API 2.0 and CNG |
| Authentication mechanisms | client authentication within TLS authentication in SOAP services own authentication mechanisms based on EDS random data |
| TLS-GOST | Embedding |
| Secure Message Formats | PKCS#7, CMS, XMLSec, SOAP (OASIS Standard 200401), S/MIME |
| Browser Integration | EDS and encryption via MS Silverlight |
| Key vaults | Registry, UBS tokens |
| Interaction with USB tokens | Key and certificate storage Using hardware implementation of algorithms Via Crypto API 2.0 |
| Applications | Microsoft Lync 2010, Microsoft Office Forms Server 2007 and Microsoft SharePoint 2010, Microsoft XPS Viewer |
| installation | Microsoft. NET has been included with Windows since Windows Vista. Support for Russian crypto algorithms requires the installation of additional software |
| Examples (GOST) | CryptoPro. NET (based on CryptoPro CSP) |
Separate Libraries
BouncyCastle is an open source library that implements its own system of cryptographic classes for the Microsoft.NET platform. The library supports both basic cryptographic algorithms GOST 28147-89, GOST R 34.10-2001, GOST R 34.11-94, and cryptographic formats PKCS#7/CMS, PKCS#10, X.509, taking into account the specifics described in the RFC of Russian manufacturers SKZI. In addition, according to the developers, the library supports the CADES format with Russian cryptographic algorithms.Java
The Java Cryptography Architecture allows you to expand the set of cryptographic algorithms supported in the platform. Given the high prevalence of Java, many of the Russian developers of cryptographic tools offer certified JCP providers.JCP
| Specification | Java Cryptography Architecture, JavaTM Cryptography Extension, JavaTM Secure Socket Extension |
| Platforms | Sun Java 2 Virtual Machine |
| Algorithms and cryptographic protocols | EDS, encryption, hash function, imitation protection, HMAC, VKO, TLS |
| Integration with PKI | X.509, PKCS#10, CMS, CRL, OCSP, TSP |
| EDS mechanisms | Class set |
| Authentication mechanisms | client authentication within TLS |
| TLS-GOST | Separate TLS provider implemented in Java according to the JavaTM Secure Socket Extension specification |
| Secure Message Formats | PKCS#7, CMS, XMLSec (eg via Apache XML Security API), S/MIME; |
| Browser Integration | Digital signature/encryption via Java applets, downloading applets via Java TLS |
| Directory service integration | with an arbitrary LDAP directory |
| Mobile platforms | Android |
| Key vaults | Registry, files, UBS tokens, MicroSD tokens |
| Interaction with USB tokens | Key and certificate storage Using the hardware implementation of cryptoalgorithms through PKCS # 11 (in Java products LCPKCS11 by Lissy and in the Java provider for Rutoken EDS by Active) |
| installation | Installer, system administrator rights required |
| Examples (GOST) | CryptoPro JCP, CryptoPro JTLS Signal-COM JCP, Signal-COM Java TLS LCJCE, LCJSSE, LCPKCS11 Java provider for Rutoken EDS Trust Java |
Java applets
One of the options for using CIPF in the browser is their integration into Java applets.In some cases, CIPF and cryptographic libraries do not require installation and are a native library. In this case, it is possible to integrate it directly "inside" the applet and call the CIPF functions through the JNI mechanism. With this scheme, the library will be installed in the user's profile when the Java applet is loaded in the browser for the first time, and its separate installation is not required.
Another option is to write a Java applet that calls the CIPF pre-installed in the system (CSP, JCP, etc.)
A more detailed example of such an implementation, based on the use of Rutoken EDS and OpenSSL, is described in the article.

Examples:
- ETP "Stroytorgy" applet (implemented in accordance with the architecture shown in the diagram)
- Remote banking system Beefit
PHP
PHP is one of the most widely used web development languages. The PHP cryptographic subsystem is built on the basis of OpenSSL, which supports Russian cryptographic algorithms. But at the same time, there is no support for Russian cryptoalgorithms in PHP itself. Some Russian manufacturers CIPF started to form a patch for PHP, which would allow the use of Russian cryptography, but this work was not completed.Binary compatibility of such CIPF as MagPro CryptoPacket with OpenSSL would make it possible to give this solution legitimacy.
Currently, many developers of information systems based on PHP use the direct call of the OpenSSL command line utility to perform crypto operations using Russian algorithms.
The exotic solution was implemented as part of the Rutoken WEB project. In the server component of the solution, GOST R 34.10-2001 signature verification is implemented directly in PHP using mathematical primitives from the native library.
Perl
Another exotic example is the implementation of encryption according to GOST 28147-89 directly in Perl http://search.cpan.org/~ams/Crypt-GOST-1.00/GOST.pm .At the same time, in real Perl projects, developers usually use command-line utility calls from OpenSSL or some Linux-compatible cryptographic information protection tool.
ruby
Ruby uses openssl as a cryptokernel, which allowed the author of this article to patch it to support Russian cryptography.JavaScript
Some time ago, an article appeared on Habré, the author of which implemented many cryptographic formats directly in JavaScriptAt the same time, crypto algorithms are used from the unified WebCrypto core, which is already supported by most modern browsers.

Problems:
- No GOSTs
- The private key is in "browser storage", not in a transferable medium
- How to connect PKCS#11 compatible devices?
Pros:
- cross-platform, cross-browser solution
- signature on the client
- PKI Support
- no installation required at all on the client
Desktop cryptographic applications
A class of applications that provide a complete windowed user interface for performing client-side crypto operations. As a rule, some CIPF is used as a crypto-core.Operations:
- file signature
- file signature verification, including chain building and revocation list verification, OCSP, timestamp verification
- file encryption, including for multiple respondents
- file decryption
- search and selection of a user certificate
- view certificate
- maintaining a database of respondent certificates, integration with the directory service (using the LDAP protocol) to search for a respondent certificate
- key pair generation, certificate request generation
- deleting a key pair
- import/export of certificates (root, user, responders)
- deleting a certificate
Examples:
- CryptoARM
- CryptoNUC
- File PRO, Admin PKI
- Blockhost EDS
- sign maker
- ViPNet Crypto File
Tools for building a trusted environment
The problem of forming a trusted environment for performing crypto-operations, in particular EDS, is a separate big topic. This article does not plan to consider it in detail, but I would like to note that conceptually, the developers go the following ways:- a separate device on which the data intended for signature is visualized and the signature itself is made after user confirmation (trustscreen)
- installation of a complex of information protection tools (MDZ, antiviruses, etc.) on the computer and client OS in order to minimize the possibility of computer infection with malware
- booting a separate trusted OS in USB-live mode
- parallel operation of the client OS and the trusted environment on different cores of one computer
I would like to dwell on the last method of forming a DS in more detail.
The Security Code company has proposed an interesting product Jinn, which allows you to emulate a trusted environment on both a multi-core and a single-core computer. Main idea this decision is that the trusted environment runs on logical cores that do not run the client OS itself. In the case of a single-core computer, now-how solutions make it possible to emulate a separate physical computing device that is not visible to the OS (or, rather, access to it from the OS is very difficult).
For the case of a multi-core computer, the trusted environment operates on 2 cores, and the client OS operates on the remaining cores. The trusted environment is loaded before loading the client OS either from a flash drive or from the Sobol electronic lock. The solution ensures that the client OS (and therefore potential malware) does not control the behavior of the trusted environment.
In fact, in the solution, two operating systems are separated by different cores of one computer and a data transfer channel is configured between them. At the same time, one of the OS (trusted environment) is designed in such a way that the options for its infection are minimized and its functionality serves the sole purpose of secure data visualization and writing.
To access the trusted environment from the client OS, a special library (COM object) is used. When signing a payment through this library, Jinn intercepts the control of the graphics adapter and renders the payment on it. If the information provided is correct, then after the user's confirmation, Jinn signs the payment order and returns control to the client OS.
July 22, 2014 08:50Cloud computing continues to transform industry after industry, appearing where it would seem least logical to appear. The process is largely reminiscent of the birth and triumphal march of computers across a diverse landscape. human activity. Today, few people think about how computers have changed the production of newspapers and magazines, production, Agriculture and especially business in all its manifestations. Now, everything around the cloud is changing in the same way, and some areas are already in the second circle. For example, accounting.
In 1994, the FAPSI Main Security Directorate developed the first electronic signature standard in Russia, but then the country was still in a very troubled time, so they really started talking about an electronic signature only 8 years later, in 2002, when a new standard for cryptographic protection of ES was approved , which actually equalizes Russian concept"electronic signature" and international - "digital signature". So the history of this technology in our country, although it has been twenty years, is actually used no more than ten.
I b O For most of this decade, the technology worked like this. On the computers of the organization (as a rule, only in the accounting department), special software was installed for working with ES, and the USB-drive contained personalized keys stored in a single copy. I must say that security in this case was provided almost complete. Without taking possession of the very "flash drive" with the keys - the token - it was impossible to sign documents on behalf of the organization. But there were also disadvantages! The token can be stolen, lost, physically destroyed - and then you will have to go through the authorization procedure in the certification center again. And if you need to sign urgent documents? In a word, cloud technologies were already on the threshold to forever change the next industry, and today the electronic document management sector can become the locomotive of their development.
We asked industry specialist Anastasia Shchepina, company analyst, to talk about the benefits of implementing EDI Synerdocs, who believes that the reluctance of businesses to switch from paper to electronic documents, from an electronic signature on a carrier to a cloud-based electronic signature in most cases is associated with fears and habits:
 “Fears must be dispelled, and established processes should be replaced with new, more efficient ones and new habits should be developed that will allow you to work and make profit faster. Concerns are usually associated with distrust of the servers that store the private keys of electronic signatures. In fact, the servers where the keys are stored are securely protected. I think this is even more reliable than carrying a token or a flash card with you. Of course, this is a matter of trust, but now cloud technologies are only developing, and certification centers are taking this seriously.
“Fears must be dispelled, and established processes should be replaced with new, more efficient ones and new habits should be developed that will allow you to work and make profit faster. Concerns are usually associated with distrust of the servers that store the private keys of electronic signatures. In fact, the servers where the keys are stored are securely protected. I think this is even more reliable than carrying a token or a flash card with you. Of course, this is a matter of trust, but now cloud technologies are only developing, and certification centers are taking this seriously.
Now about habits. Many articles have already been written about the advantages of electronic document management, there is no secret here. Cloud-based electronic signature adds advantages: it allows you to reduce the cost of acquiring electronic signatures, makes it possible to sign documents at any time and in any place where there is an Internet connection. As a result, it turns out that the competitors of a conservative company, who are open to new technologies, make their business more efficient and get competitive advantage. This can force the business to start moving first to electronic document management using an electronic signature on a carrier, and later, possibly, to cloud-based electronic signatures.”
How does the usual ES technology look like in the cloud? The certification authority creates your electronic signature and stores it in its own cloud. No tokens are needed in this case: authorization occurs via SMS, through the linked mobile phone. The signature itself is located in the cloud, so you can sign invoices and other documents from any device with Internet access: from an office computer, from a personal laptop, from a tablet or even a smartphone. This approach has obvious advantages. According to Synerdocs analyst Anastasia Shchepina, there are two main advantages of a cloud-based electronic signature.
1. Its cost is lower. Purchasing a cloud-based electronic signature requires less costs than buying in the normal mode. This is due to the fact that in order to work with this signature, it is not necessary to purchase a carrier and a means of cryptographic information protection (hereinafter referred to as CIPF). In the case of a cloud-based digital signature, the CIPF is located only on the server where the private key is stored. All this is formalized by appropriate agreements and powers of attorney.
2. Mobility. Now the Internet is available almost everywhere, which means that you can sign documents with a cloud-based electronic signature from any tablet, smartphone, device that supports Internet access. Neither paper nor an electronic signature on a carrier gives such an opportunity. CIPF for mobile devices is, of course, being developed now, but it is easier to work without CIPF on your device at all. Besides, private key cloud ES will not have to be installed by you personally or paid to a CA employee who will set everything up. There will be no need to train users to work with CIPF and ES certificates.

But, having a mass positive qualities, the cloud signature also has negative aspects. Despite the fact that more than 100,000 cloud ESs have already been issued through popular accounting services in 2013, the widespread use of signatures is still in question. Anastasia Shchepina believes that the business has not yet fully decided on the technical component of using cloud ES:
If we talk about cloud-based ES in the workflow, it is not yet clear how it will work with several EDI services. Most likely with great difficulty. The private key is stored on the CA server, the EDI service needs to make a request there to generate an electronic signature. At the moment, not all services will be easily integrated with the software of the CA, you will have to take this into account when switching to a cloud signature. You may have to buy a separate signature for each service.
The second minus is rather from the conceptual area. The essence of an electronic signature implies the replacement of a handwritten one: that is, you personally, with my own hands sign the document with the private part of the key. It should be yours and yours alone. In the cloud version, the private key is not in your hands - but somewhere out there, on the CA server. That is, in fact, you sign not with your own hands, but through an intermediary. Of course, all this will be documented, and the servers themselves will be securely protected, but not in all organizations the security service will approve this. If it is important for you that the owners of the private keys themselves sign the documents, then the cloud-based electronic signature will not suit you.
In general, the prospects for cloud ES and electronic document management in our country are encouraging. The State Duma has already approved the development plan e-government until 2018, which includes a number of measures to promote business. For example, "a decrease in the average number of requests from representatives of the business community to a state authority to receive one public service." And although the thesis does not sound very impressive, since the number of applications is planned to be reduced to only two, this is already some progress leading us to the European scenario. That is, such a situation when it will be possible to open a business, pay taxes and sign any documents on the Internet, and often from a smartphone.
In the traditional understanding of the electronic signature (ES), which is familiar to the vast majority of users, the key of this very signature is stored by its owner. Most often, some protected key carrier in the form of a USB token or smart card that the user can carry around. This key carrier is carefully guarded by the owner from unauthorized persons, since the key falling into the wrong hands means its compromise. To use the key, specialized software (CIPF) is installed on the owner's device, designed to calculate the ES.
On the other hand, in the IT world, the concept of "cloud computing" is increasingly being used, which in many ways has a lot of advantages compared to using traditional applications installed on the user's computer. As a result, there is a completely natural desire to take advantage of these advantages of cloud technologies to create "ES in the cloud".
But before solving this problem, it is necessary to define what we mean by "electronic signature in the cloud". Currently, in different sources you can find different interpretations of this concept, often suitable only for explaining on the fingers to a person "from the street" who went to the Certification Center to "buy an electronic signature".
What is a qualified electronic signature in the cloud
For the purposes of this article, as well as other popular science and practical discourses on cloud electronic signature, it is proposed to use the following definition.
An electronic signature in the cloud (cloud electronic signature) is a computing system that provides access via the network to the possibilities of creating, verifying ES and integrating these functions into business processes of other systems.
In accordance with this definition, a local ES tool can also be used for a cloud-based electronic signature. For example, using the user through a web browser can sign an electronic document using the ES tool installed on his terminal device ( Personal Computer or tablet). In such a system, the signature key remains with the owner and security issues are resolved using a standard set of tools known in the world as "traditional ES". You can call it if you like cloud ES with local ES tool.
Another version of the cloud ES is obtained with using an ES tool hosted in the cloud. For the convenience of further presentation, let's call such a schemecompletely cloud-basedto distinguish it from the previous one. This scheme regularly causes heated discussions among specialists, since it involves the transfer of the signature key itself “to the cloud”. This article is intended to clarify a number of issues related to the security of a completely cloud-based ES.
Let's start with the main
The main headache when transferring any IT system “to the cloud” is the pain of “security officers” (and lawyers helping them) associated with the transfer of information “there” for processing or storage. If earlier this information did not leave some protected perimeter, and it was relatively easy to ensure its confidentiality, then in the cloud the very concept of the perimeter is missing. At the same time, the responsibility for ensuring the confidentiality of information is, in a sense, “blurred” between its owner and the cloud service provider.
The same thing happens with the ES key transmitted to the cloud. Moreover, the ES key is not just confidential information. The key must be available only to one person - its owner. Thus, trust in a cloud signature is determined not only by the personal responsibility of the user, but also by the security of storing and using the key on the server and the reliability of authentication mechanisms.
Currently, certification tests of our solution are being carried out. This is a cloud ES server that stores user keys and certificates and provides authenticated access to them to generate an electronic signature. Both of the above-mentioned aspects of the security of cloud-based ES in particular are the subject of research conducted during the testing of CryptoPro DSS. At the same time, it is worth noting that a significant part of these issues has already been considered in the framework of case studies. , on which CryptoPro DSS is based.
In our country, the organizational and legal aspects of using cloud ES are still poorly developed, so in this article we will consider CryptoPro DSS from the point of view of the requirements for the signature server developed by the European Committee for Standardization (CEN).European way
October 2013 The European Committee for Standardization (CEN) approved the technical specification CEN/TS 419241 "Security Requirements for Trustworthy Systems Supporting Server Signing". This document requirements and recommendations are given for an electronic signature server designed to create, among other things, qualified signatures.
I would like to note that even now CryptoPro DSS fully complies with the requirements of this specification in the strongest version: the Level 2 requirements for the formation of a qualified electronic signature (in terms of European legislation).
One of the main requirements of Layer 2 is to support strong authentication options. In these cases, the user is authenticated directly at the signing server - as opposed to being allowed for Level 1 authentication by an application that accesses the signing server on its own behalf. All authentication methods supported by CryptoPro DSS satisfy this requirement Level 2
In accordance with this specification, user signature keys for the formation of a qualified ES must be stored in the memory of a specialized secure device (cryptographic token, HSM). In the case of CryptoPro DSS, such a device is the CryptoPro HSM cryptographic hardware and software module - certified by the FSB of Russia at the KB2 level as an ES tool.
Authentication of the user on the digital signature server to meet the requirements of Level 2 must be at least two-factor. CryptoPro DSS supports a wide, constantly updated range of authentication methods, including two-factor ones. In addition to the usual cryptographic tokens, a specialized smartphone application, such as one-time password generators (OTP tokens), can also be used as an authentication tool. The CEN document also mentions these methods.
Another promising method of Layer 2 authentication could be the use of a cryptographic application on the SIM card in the phone. In our opinion, this option The use of SIM-cards with cryptography is most realistic, since the construction of a functionally complete cryptographic information protection tool (or ES tool) according to the new requirements of the FSB based on only a SIM-card is hardly possible.
Considered data sheet also allows the use of an electronic signature server to generate signatures for a certain set of documents at once. This opportunity can be useful when signing a large array of homogeneous documents that differ only in data in a few fields. In this case, user authentication is performed once for the entire package of documents. Support for this use case is also available in CryptoPro DSS.
The CEN document also contains a number of requirements for the formation, processing, use and deletion of user key material, as well as for the properties of the internal key system of the electronic signature server and for auditing. These requirements are fully and even "with a margin" covered by the requirements for ES tools of class KB2, according to which the CryptoPro HSM PACM, which is responsible for these issues, is certified.
Our future
The CryptoPro DSS solution supports a wide range of authentication methods, among which it is possible to choose the right one for each task. The reliability of the safest of them meets the most stringent criteria of European requirements CEN / TS 419241 and, as we expect, in the near future will be confirmed by a certificate of conformity from the FSB of Russia.
Alexey Goldbergs,
deputy technical director
LLC "CRYPTO-PRO"
Stanislav Smyshlyaev, PhD,
head of information security department
LLC "CRYPTO-PRO"
Pavel Smirnov, Ph.D.,
Deputy Head of Development Department
LLC "CRYPTO-PRO"
As you know, the task of an electronic signature is to simplify the workflow. According to the 2011 law "On Electronic Signature", a digital document that is signed by an ES is equated to a paper document with a hand-made autograph.
“A “cloud” electronic signature has all the properties of a regular one, only it is stored not on a flash drive or computer, but on the Internet - on a special secure server, “in the cloud,” says Igor Chepkasov, founder and president of the National Cryptocurrency Development Fund. The signing and encryption of the document also takes place there, therefore such an electronic signature does not require the installation of special software on the computer. The expert notes that one of the advantages of the "cloud" signature is the ability to sign documents (including reporting) and send them from anywhere in the world and from any device.
Anton Elikov (Merkat project) notes that an electronic signature “in the cloud” is something that many of us use every day without even noticing. “The most striking example is the authorization mechanism in mobile and Internet banks, when, after entering a password, you are sent a one-time PIN code via SMS. Such a two-level authorization, in essence, can already be an electronic signature, ”says the expert.
Why do you need e-mail. Sergey Kazakov, an expert in the field of information security at SKB Kontur, recalls that with the help of electronic signatures, companies submit reports to the tax and other regulatory authorities, and conduct electronic document management. Digital signature also widely used in the field public procurement. “According to our estimates, the total number of electronic signature users in Russia exceeds two million,” the expert notes. “The technology of “cloud” electronic signature, which appeared several years ago, makes this tool more accessible for business. This is confirmed by several tens of thousands of SKB Kontur customers who have made a choice in its favor,” says Mr. Kazakov.
note
While experts are talking about the spread of "cloud" ES, there is one problem - the issues of its application are not spelled out in regulations.
As Aleksey Dashkov, head of information security at System Software, notes, an ES performs the same function as a stamped signature. “It ensures the authenticity of the document and consists of a private and a public key. The document is signed using a private key, which is usually stored on a special medium - a token. You can buy a service from a number of companies providing such services, no special requirements, except for the availability of a standard set of constituent documents, are required,” he says.
“The “cloud” electronic signature is a regular electronic signature, but with one difference: the private key is stored on the servers of the certification center, and the signing of documents is carried out there. The signer's identity is usually verified by sending an SMS with a code to a mobile phone,” explains Mr. Dashkov.
Issue price
Igor Chepkasov said that the cost of an EP depends on its functionality and scope and ranges from 1,000 to 15,000 rubles. “At least, I personally met such prices when I needed an EP for work. A “cloud” electronic signature in some companies I know costs 3,000 rubles,” the expert shares.
The cost of a "cloud" signature varies for different operating companies. You can find an offer for 900 rubles a year. However, do not unconditionally believe advertising promises. We advise you to familiarize yourself with the price list for the "cloud" signature in detail and find out what is included in the price, and only after that make a decision on its purchase.
“The cost of a “cloud” electronic signature is usually included in the tariff of the service that the client buys. The only SKB Kontur service that sells it separately is the Diadok electronic document management system. In it, it is 900 rubles. At the same time, a regular certificate on a carrier with a license on a cryptographic information protection tool (CIPF) will cost 3,000 rubles, ”says Sergey Kazakov.
How does it work?
The technology is based on a specialized electronic signature server located "in the cloud". “If the user needs, for example, to send a report to tax office, its accounting system interacts with the electronic signature server and sends it a document to be signed. The electronic signature server is obliged to request permission from the user - this can be done by sending the transaction confirmation code to his mobile phone, as in the Internet bank, ”says Sergey Kazakov. By entering the confirmation code in the accounting system, the user authorizes access to the ES key, and a signature is created for the document. “All electronic signature keys are stored in encrypted form on a specialized device that meets the most stringent security requirements. The operator of the electronic signature server must take all measures to minimize the risk of unauthorized access to the keys,” says Mr. Kazakov.
In order to use a "classic" electronic signature, you need to purchase a token and specialized software - a cryptographic provider. “This is a significant expense, especially for start-up entrepreneurs. Then this software needs to be installed and configured, and if you are going to use the signature on several workstations - for each place separately. A “cloud” electronic signature does not require the purchase of software and pre-configuration, it cannot be lost or forgotten,” says Mr. Kazakov. Unlike traditional technologies, the "cloud" signature is available to users on any operating system and platform, including on mobile devices.
Alexey Dashkov notes that "cloud" ES are popular with small companies or individual entrepreneurs actively using services “such as online accounting and online document management”. IN large organizations who do not use "clouds", the use of such a signature, according to him, may be more expensive and more difficult than the use of a conventional ES.
What are the prospects?
According to Anton Elikov, the entire transport industry in Russia is waiting for the spread of the use of "cloud" electronic signatures. “One has only to imagine a situation when a forwarding driver goes on a flight not with a bundle of papers, but with a tablet. And right at the place of shipment, he signs a consignment note with the client! But the “cloud” electronic signature could bring the main benefit in the case when the delivery document differs from the actually shipped volume of products (re-grading, breaking during transportation),” he notes. According to Mr. Elikov, such cases in practice sometimes happen up to 40 percent. “And all these documents are now sent on a long journey of interaction between the accounting departments on the part of the supplier and the buyer. Although the issue of discrepancies could be settled right at the place of shipment, and the fact of the change would be confirmed by a “cloud” signature,” the expert concludes.
Igor Chepkasov says that at present there are already completely new developments using Blockchain technology, namely smart contracts. “Decentralization, the fundamental principle of the technology, provides absolute protection against compromise and unauthorized access to any document and the signature itself, since each such block element (signature, document, archive, etc.) is located in a strong chain of numbered blocks protected by the most complex cryptographic code,” he says. According to Mr. Chepkasov, it is impossible to make changes to a block already put into circulation; a smart contract is an electronic algorithm that describes a set of conditions, the fulfillment of which entails certain events. “His work is based on the creation and application of so-called low-trust protocols, where the protocol algorithm uses only software tools, and the human factor is excluded from the decision-making chain as much as possible - a person here acts exclusively in ro and one of the parties involved in the implementation of the contract. For example, when sending payments, the execution of a contract is impossible without receiving the number of electronic signatures specified in the contract,” he notes.
In the meantime, while experts talk about the spread of the practice of using a "cloud" electronic signature and talk about the possibilities for developing technologies, there is one problem. It is connected with the fact that today the issues of applying such an ES are not properly spelled out in the regulations. But soon, namely, in the third quarter of 2016, Russians will have the legal opportunity to use an electronic signature without a physical medium - a USB flash drive or a SIM card. Such a norm is contained in the "road maps" for the program for the development of the Internet in Russia, which the Internet Development Institute prepared for the President of the Russian Federation. So we can expect that companies will soon stop being afraid of "cloud" technologies and begin to use such an electronic signature more actively in their work.